Author
Published
20 Mar 2025Form Number
LP2183PDF size
15 pages, 978 KBAbstract
Intel’s Software Guard Extensions (SGX) is a security feature designed to safeguard user data privacy. It leverages hardware extensions, including a new set of instruction extensions and access control mechanisms, to enable isolated operation between programs. This ensures the confidentiality and integrity of sensitive code and data, protecting them from malware attacks. With SGX, even if an attacker gains access to the operating system, they cannot retrieve sensitive data, making it highly suitable for security-critical applications.
This paper provides an overview of the technical principles behind SGX, its implementation, enabling processes, how to build and validate SGX environments, and troubleshooting during setup. It is aimed at Linux administrators interested in leveraging SGX to create secure container environments on ThinkSystem servers.
Note: This paper focuses on how to enable SGX at the OS software level. It is a partner to the Lenovo Press paper Enabling Intel SGX on Lenovo ThinkSystem Servers which provides hardware information and the details on how to enable Intel SGX in the UEFI settings of ThinkSystem servers. The two papers can be used together to provide a broader understanding of how to implement Intel SGX on ThinkSystem servers running Linux.
Introduction
In the current landscape of pervasive security threats, ensuring the confidentiality and integrity of sensitive information is of paramount importance. Traditional software security measures often fall short in protecting data from sophisticated attacks that exploit system vulnerabilities. Intel SGX addresses this challenge by providing hardware-based security mechanisms that isolate sensitive computations and data from the rest of the system.
SGX introduces the concept of enclaves-secure regions of memory that are protected even from privileged system software. These enclaves ensure that sensitive data and code can be executed in a secure environment, free from tampering and eavesdropping. This technology is used in the scenarios of where secure data processing and confidentiality are crucial, such as in financial transactions, healthcare data processing, and confidential communications.
This paper has the following topics:
- High-level introduction to Intel SGX, its purpose, importance, and the issues it aims to solve.
- SGX functionalities, architecture, and insights.
- How to enable Intel SGX on Lenovo systems, overview of configuration on UEFI settings and operating system settings.
- How to build SGX test environment and validate whether SGX is correctly enabled.
- SGX support information.
- Troubleshooting when building environment and testing SGX.
For our test environment, we used RHEL 9.4 on a ThinkSystem SR630 V4 server with Intel Xeon 6787P processors.
Understanding Intel SGX
Intel SGX is designed to enhance data protection and improve the security of application code. This hardware-based CPU defense mechanism allows applications to operate within a private memory space, pre-allocated to specific areas of RAM. SGX introduces the concept of an Enclave, a secure environment with its own privileged mode of execution. This ensures that even high-privilege software, such as the operating system or BIOS, cannot access the data safeguarded by SGX.
When developing an Intel SGX application, programmers can decide which parts of the code should be placed inside an enclave and which should remain outside. They can designate certain sections as the "trusted part," responsible for handling sensitive data and private code segments, while the rest of the code operates as the "untrusted part". The untrusted part functions are similar to non-SGX applications and can be accessed by other high-privilege software.
The following is the complete workflow of an SGX application.
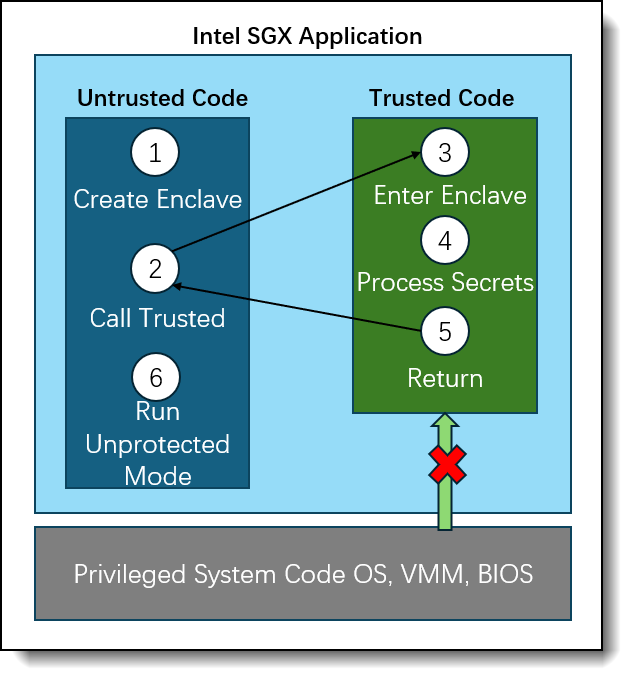
Figure 1. Workflow of an SGX application
Building an SGX application requires developers to modify their code. When the application is running, the following workflow is executed:
- Application runs and uses “sgx_create_enclave” to create a new enclave region. This enclave region is used to store the code segments and data.
- Application uses “Ecalls” to execute the trusted function.
- Application execution is transitioned to the enclave mode.
- Application execution,code segments and data are allowed to be accessed in the enclave memory. Any external access to the enclave memory is denied.
- The application uses "Ocalls" for function returns, and the enclave data remains within the trusted memory.
- Continue to run the unprotected code.
SGX technology insights
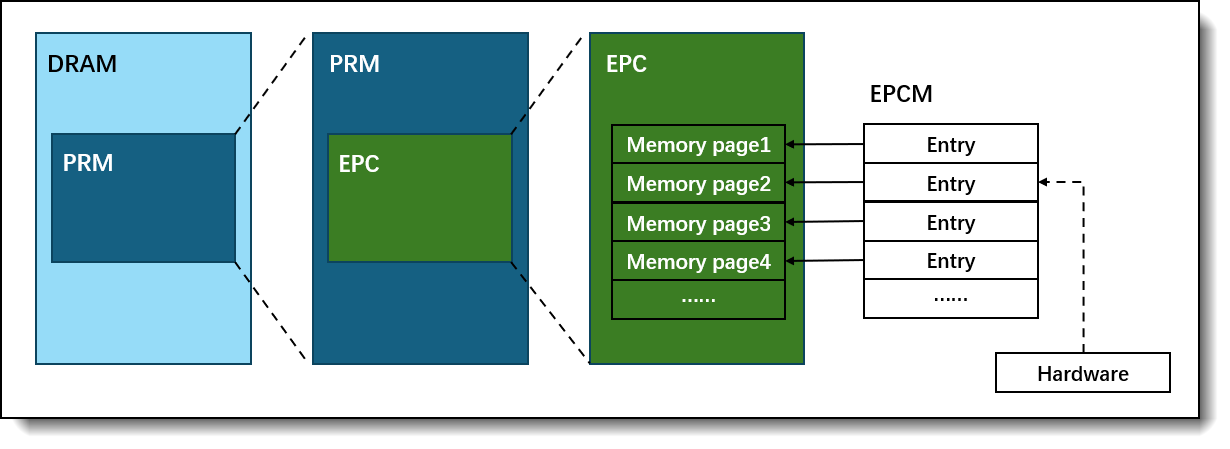
The software isolation environment provided by SGX is mainly achieved through a special memory management mechanism. The following is an introduction to SGX-specific terminology.
- DRAM (Dynamic Random-Access Memory): CPU memory.
- PRM (Processor Reserved Memory): The pre-reserved memory on DRAM used by SGX.
- EPC (Enclave Page Cache): The PRM memory organized in pages, each page is 4k generally.
- EPCM (Enclave Page Cache Map): record allocations for each EPC page, permission recording and page access control.
When SGX is enabled in the BIOS, the BIOS will reserve a section of memory in DRAM by configuring a set of range registers called PRM. This continuous memory space is at the lowest BIOS level and cannot be accessed by other software including system software. The processor's memory controller safeguards data by blocking peripheral devices from directly accessing PRM memory.
EPC is a collection of 4KB memory allocated by the operating system in PRM to load application data and code segments. Each EPC page can only be assigned to one enclave at a time and only be accessed from inside an enclave. To avoid the untrusted system software allocates the EPC pages to enclaves, the trusted hardware needs to check each EPC entry allocation record.Any unauthorized software requesting access to the EPC page will cause the processor to issue a fault and deny access. The allocation records for EPC entries are stored in the corresponding EPCM entries, maintaining a one-to-one mapping relationship.
The EPCM serves as the gateway to the EPC, storing control information for EPC pages. Similar to a page table in an operating system, it manages key details about EPC pages, such as their usage status, ownership, page types, address mapping, and permission attributes. The EPCM is not directly accessible by software; instead, it is accessed through a hardware module called the Page Miss Handler (PMH). The PMH performs normal accesses to EPC pages by referencing the page table, range registers, and EPCM data, while blocking any unauthorized or abnormal access attempts.
Enabling Intel SGX on ThinkSystem servers
Tip: For details of enabling Intel SGX on ThinkSystem servers, see the Lenovo Press paper Enabling Intel SGX on Lenovo ThinkSystem Servers.
The SGX feature can be enabled by the following steps:
- In System Setup (F1 at boot), enter the UEFI System Configuration and Boot Management as shown in the following figure:
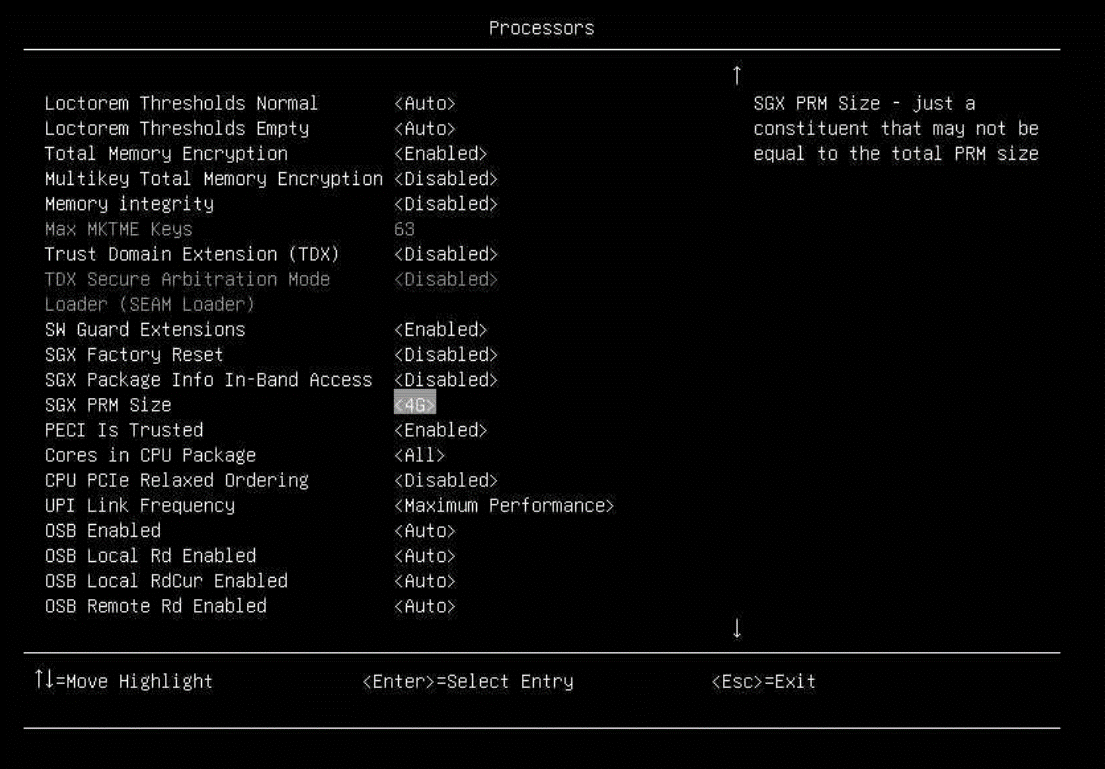
- From the BIOS setup menu path, do the following operations, as shown in the following figure.
System Settings → Processors → SW Guard Extension to enable SGX feature.
System Settings → Processors → SGX PRM Size to pre-reserve SGX memory.
- For 3rd Gen Scalable processors, there is an extra configuration needs to be set:
System Settings → Processors → Total Memory Encryption (TME) to set TME enable.
For detailed UEFI and HW configurations, refer the Lenovo Press paper Enabling Intel SGX on Lenovo ThinkSystem Servers.
Testing and Validating SGX
This section primarily focuses on the OS level, verifying from the software layer whether the hardware properly supports SGX and how to build and use SGX-secured enclaves to test and validate SGX functionalities.
In this section:
Hardware support check
This process describes downloading and compiling SGX hardware tools, checking SGX version support, verifying SGX device availability, inspecting kernel-enclave reserved memory, and performing CPUID checks. These checks ensure that the hardware and UEFI fully and correctly support SGX.
- Download SGX Feature Detection Tool.
# git clone https://github.com/ayeks/SGX-hardware.git - Install SGX Feature Detection Tool Dependency Packages.
# yum install git make gcc libcap-devel - Compile SGX Tool.
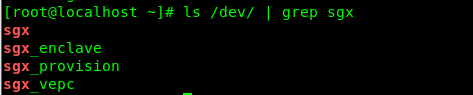
# cd SGX-hardware/ && make - Make sure SGX device, memory and feature are all in good working order. When SGX is functioning properly, four device nodes should be visible under the /dev/ directory.
# ls /dev | grep sgxFour devices are listed below:
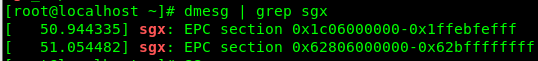
- Pre-reserved memory: Make sure the operating system reserves memory. A record of the reserved EPC section should appear in the dmesg logs, confirming that the kernel has successfully allocated memory for SGX enclaves.
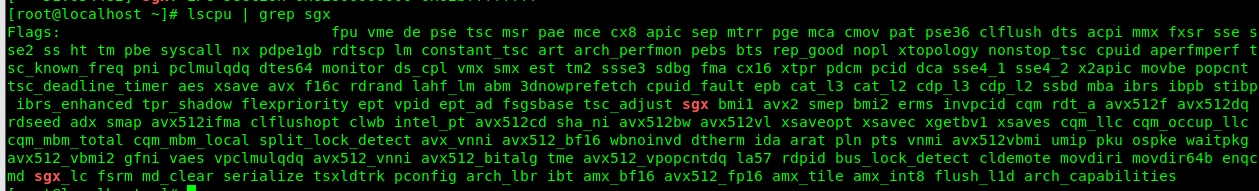
# dmesg | grep sgx - CPU instruction support: “sgx” and “sgx_lc” flags must be enabled. The two CPU flags indicate that SGX is supported at the hardware level by the CPU, and SGX has been enabled in the UEFI settings.
# lscpu | grep sgx - SGX Detection Tool test. This tool executes the CPUID instruction to read the values of the EAX, EBX, ECX, and EDX registers, extracting SGX version support and hardware capability information from the CPU feature registers. The “Support SGX” entries must be 1 to ensure proper functionality of SGX-related CPU instructions. If the values aren’t “1”, check the hardware compatibility (CPU and memory slots) for SGX support and UEFI configurations.
# ./test-sgx
SGX test suit verification
The SGX test suite requires both SGX-SDK and SGX-PSW. Since the compilation and installation of SGX-PSW depend on the SGX-SDK, the SGX-SDK must be installed first, followed by the SGX-PSW.
- Download SGX test suit.
# git clone https://github.com/intel/linux-sgx.git - Install test suit dependency.
# yum install ocaml ocaml-ocamlbuild wget python3 openssl-devel git cmake perl kernel-devel # yum groupinstall 'Development Tools' # yum install openssl-devel libcurl-devel protobuf-devel cmake rpm-build createrepo yum-utils pkgconf boost-devel protobuf-lite-devel systemd-libs - Compile preparation.
# cd linux-sgx && make preparation # cp external/toolset/rhel8.6/* /usr/local/bin/OS needs to find the copied toolset under /usr/local/bin/, you can use the following command to check.
# which ar as ld objcopy objdump ranlib - Compile SGX-SDK.
# make sdk && make sdk_install_pkg - Install SGX-SDK.
# cd linux/installer/bin/ && ./sgx_linux_x64_sdk_[version].binsgx_linux_x64_sdk_[version].bin will be generated under the path of linux/installer/bin/ after compilation.
When asking the installation path, you can input the path such as "/opt/intel/".
- Source environment.
# source /opt/intel/sgxsdk/environment - Verify SGX-SDK.
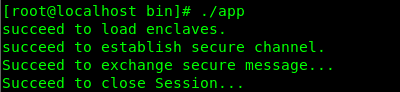
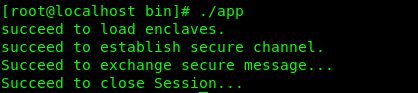
# cd /opt/intel/sgxsdk/SampleCode/LocalAttestation/ # make SGX_MODE=SIM # cd bin && ./appIf SDK is in good working order, it will show the following message:
- Compile SGX-PSW.
# cd /path/to/linux-sgx && make psw && make psw_install_pkg # cd psw/ae/le && make - Install SGX-PSW.
# cd linux/installer/bin/ && ./sgx_linux_x64_psw_[version].binsgx_linux_x64_psw_[version].bin will be generated under the path of linux/installer/bin/ after compilation.
- Verify SGX-PSW.
# cd /opt/intel/sgxsdk/SampleCode/LocalAttestation/ # make # cd bin && ./appIf SDK is in good working order, it will show the following message:
Support Scope
This section lists the kernel and OS distributions/versions that support Intel SGX.
The following kernel versions support Intel SGX:
- Kernel version 5.11 or later.
Supported Intel platforms:
- 3rd Gen Intel Xeon Scalable processors or later
The following 64-bit operating systems support Intel SGX:
- Ubuntu 20.04 LTS Desktop, or later
- Ubuntu 20.04 LTS Server, or later
- Ubuntu 22.04 LTS Server, or later
- Ubuntu 23.10 Server, or later
- Red Hat Enterprise Linux Server 9.2, or later
- CentOS Stream 9, or later
- CentOS 8.3, or later
- SUSE Linux Enterprise Server 15.4, or later
- Anolis OS 8.6, or later
- Debian 10, or later
Troubleshooting
This section lists common issues you might encounter during your testing, and recommended methods to resolve the problems.
- No “sgx” on lscpu flags
This indicates that SGX has not been successfully enabled; perform the following checks:
- Whether CPU platform supports SGX
- Whether the location and quantity of physical memory modules meet the requirements
- Whether UEFI configuration is correct
- SGX-hardware test shows SGX1 leaf or SGX2 leaf is 0
This indicates that SGX is supported on this platform but not enabled correctly.
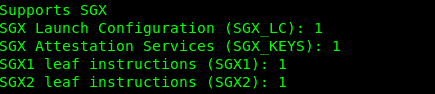
You will get the following test results if you execute “./test_sgx”:
SGX Launch Configuration (SGX_LC): 1 SGX Attestation Services (SGX_KEYS): 0 SGX1 leaf instructions (SGX1): 0 SGX2 leaf instructions (SGX2): 0If execute “dmesg | grep sgx”, you will also get the following
There are zero EPC sections.Verify if there are any issues with the CPU hardware. If necessary, consider replacing the CPU.
- Compile Errors during building SGX test suit
Perform the following check:
- Whether all dependent packages are installed.
- Whether the network can connect to Github,the SGX test suit needs additional dependent packages to be pulled from GitHub for compilation.
- Whether c++ std version meets the SGX test suit requirements (The default requirement is c++ std 11, but on some newer OS versions, the default c++ std is 14. Modify the target directory CMakeLists.txt as "set(CMAKE_CXX_STANDARD 14)" to solve this issue).
- “./app” shows “failed to load enclave”
If the kernel version is greater than 5.11 and the hardware platform supports SGX, execute “./app” still report “failed to load enclave”, then try referencing this link (https://download.01.org/intel-sgx/latest/linux-latest/docs/Intel_SGX_SW_Installation_Guide_for_Linux.pdf) and using the pre-build version to retry. This failure might be caused by SGX test suit version or dependencies.
References
See the following web pages for more information:
- General overview of Intel SGX
https://sys.cs.fau.de/extern/lehre/ws22/akss/material/intel-sgx.pdf - Intel SGX for Linux on github
https://github.com/intel/linux-sgx?tab=readme-ov-file - What is Intel SGX and What are the Benefits?
https://phoenixnap.com/kb/intel-sgx - Intel SGX - Reduce the Attack Surface Around Your Data to Unlock New Opportunities
https://www.intel.com/content/www/us/en/products/docs/accelerator-engines/software-guard-extensions.html - Wikipedia - Intel SGX
https://en.wikipedia.org/wiki/Software_Guard_Extensions - Enabling Intel SGX on Lenovo ThinkSystem Servers
https://lenovopress.lenovo.com/lp1471-enabling-intel-sgx-on-lenovo-thinksystem-servers - Intel SGX Software Installation Guide For Linux OS
https://download.01.org/intel-sgx/latest/linux-latest/docs/Intel_SGX_SW_Installation_Guide_for_Linux.pdf
Author
Dong Wang is a Linux engineer in the Lenovo Infrastructure Solution Group in Beijing, China.
Thanks to the following people for their contributions to this project:
- Adrian Huang
Trademarks
Lenovo and the Lenovo logo are trademarks or registered trademarks of Lenovo in the United States, other countries, or both. A current list of Lenovo trademarks is available on the Web at https://www.lenovo.com/us/en/legal/copytrade/.
The following terms are trademarks of Lenovo in the United States, other countries, or both:
Lenovo®
ThinkSystem®
The following terms are trademarks of other companies:
Intel®, the Intel logo and Xeon® are trademarks of Intel Corporation or its subsidiaries.
Linux® is the trademark of Linus Torvalds in the U.S. and other countries.
Other company, product, or service names may be trademarks or service marks of others.
Configure and Buy
Full Change History
Course Detail
Employees Only Content
The content in this document with a is only visible to employees who are logged in. Logon using your Lenovo ITcode and password via Lenovo single-signon (SSO).
The author of the document has determined that this content is classified as Lenovo Internal and should not be normally be made available to people who are not employees or contractors. This includes partners, customers, and competitors. The reasons may vary and you should reach out to the authors of the document for clarification, if needed. Be cautious about sharing this content with others as it may contain sensitive information.
Any visitor to the Lenovo Press web site who is not logged on will not be able to see this employee-only content. This content is excluded from search engine indexes and will not appear in any search results.
For all users, including logged-in employees, this employee-only content does not appear in the PDF version of this document.
This functionality is cookie based. The web site will normally remember your login state between browser sessions, however, if you clear cookies at the end of a session or work in an Incognito/Private browser window, then you will need to log in each time.
If you have any questions about this feature of the Lenovo Press web, please email David Watts at dwatts@lenovo.com.